1 Introduction
SAFR Mobile Credentials offers increased security through a 2-factor authentication without the inconvenience of having to present 2 separate credentials to the reader. While SAFR Mobile credentials includes a 2nd credential (mobile phone), users do not need to take an explicit action to present that credential to the reader. The user can leave the mobile phone in the pocket or bag and it will automatically transfer the credential to SAFR SCAN.
SAFR Mobile Credentials also offers increased privacy by limiting the distribution of PII (personally identifiable information). The user’s PII stays with the user, not with the access control hardware device. It does this by capturing the face image and biometric signature of the face on the phone and transferring that information to a trusted SAFR SCAN device only when within range. When the user moves their phone out of range of SAFR SCAN, the PII is discarded.
2 How it works
SAFR Mobile Credentials users 2 factors to authenticate:
- User’s face
- A trusted Mobile Credential unique to each user
Both factors are required to trigger and Access Granted event. When a person is within 20 feet (7 meters) of SAFR SCAN, their phone will automatically transfer the user’s mobile credential to SAFR SCAN. SAFR SCAN authenticates the Mobile Credential, holds this credential, and monitors for the user’s face. When the user approaches SAFR SCAN and present’s their face, SAFR SCAN authenticates their face and issues an Access Granted event.
SAFR Mobile Credentials are managed by SAFR Key SAFR Key for Android or iOS. SAFR Key creates and stores each user’s Mobile Credential securely on the user’s personal device. Users are prompted to install SAFR Key and create their mobile credential as part of the invitation flow described below.
SAFR Mobile Credentials use the PKOC (Public Key Open Credential) standard. SAFR is interoperable with mobile credentials created by other manufactures. SAFR and SAFR 2.0 Mobile Credentials offer enhanced capability such as embedded PII data.
SAFR Mobile Credentials offers two modes of operation.
-
Distributed Factors – Face and/or access card id are loaded via ethernet.
- Both face and credentials are transferred from the PACS (Physical Access Control System) Software to SAFR Server and transmitted to SCAN over Ethernet.
-
Embedded Factors – Face and/or access card id are loaded into SAFR SCAN via Bluetooth
- Users face image is captured on the phone and transmitted directly to SAFR SCAN via the phone’s Bluetooth only during access transactions.
2.1 SAFR Mobile Credentials with Distributed Factors
2.1.1 Invitation Flow
The diagram below describes the flow for SAFR Mobile Credentials with Distributed Factors.

Users are granted a mobile credential through an invite flow. Before the invite flow, the distributed method requires that face and credentials be copied from the PACS to SAFR Server.
The invite include a link that the user will use to initiate the credential registration. If the user does not already have the SAFR Key App, they will be prompted to install it from the App/Play Store. Once installed, the user can click the link again to create the credential. If enabled, the credential is then transmitted to SAFR Server or SAFR Cloud via the SAFR Cloud bridge. Finally, the credential is synchronized to the person record on SAFR SCAN where it is then ready to use as the 2nd authentication factor.
2.1.2 Authentication Flow
Below figure shows the authentication flow.

As long as the SAFR Key application is allowed to run in the in the background, the user’s Mobile Credential is automatically transmitted to SAFR SCAN when in range. The user then only need to present their face which signals intention and the user’s access card credentials are sent to the control panel.
2.2 SAFR Mobile Credentials with Embedded Factors
The diagram below describes the flow for SAFR Mobile Credentials with Embedded Factors.

The flow is similar to Distributed except that card number is encrypted into the invite and face is collected on the user’s mobile phone and stays there along with the card number. The mobile credential (without embedded factors) can still be transmitted back to the user records if desired.
2.2.1 Authentication Flow
Below figure shows the authentication flow.

Works much the same way as Distributed but mobile credential includes face and optionally the card number.
2.3 Mobile Credential QuickStart
Following describes how to get started right away with SAFR Mobile Credentials.
Either in SAFR Desktop or SAFR Server Web Console, Enable SAFR Cloud Connect as follows:
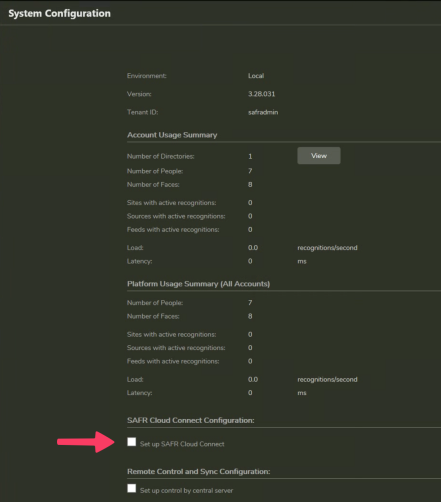
- Open SAFR Desktop > Tools menu > System Configuration (or open http://localhost:8090/status)
-
Scroll down to SAFR Cloud Connect Configuration
-
Check “Set up SAFR Cloud Connect”.
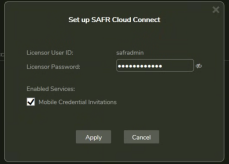
- Enter Licensor password and check “Mobile Credential Invitations”
Either in SAFR Desktop or SAFR SCAN Web Console, perform following:
-
Set Access Mode in Operation > Access Control as follows:

-
Enable SAFR Mobile Credentials in System > Mobile Credentials

-
Configure as follows:
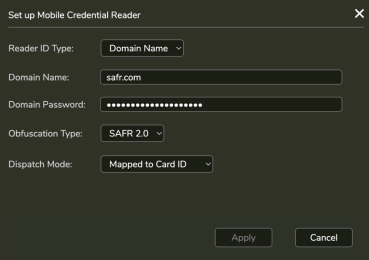
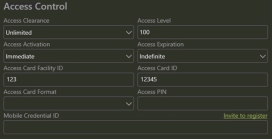
- Open Person Record send invite
|
Click “Invite to register” |
Complete as follows: |
|
|
|
- An email will be opened with invitation link. Click “Send”.
-
Open the email on Android or iOS phone, click the link and click Accept.
If prompted, accept Android/iOS Location and Nearby Devices permissions.
|
Accept Invite |
Snap Photo |
Review Photo |
Invite Accepted |
|
|
|
|
|
2.4 SAFR Key Application
2.4.1 Background Operation
SAFR Key application can be granted permission to run in the background. This occurs shortly after installation. The user is prompted to allow SAFR Key to access device Bluetooth either while the app is running or always. If always granted, SAFR Key will automatically interact with SAFR SCAN device when in range (about 15 to 20 feet or 5 to 7 meters).
2.4.1.1 About Android Phones
Not all Android phones operate the same. While most Android phones will run continuously in the background, some will turn off the Bluetooth receiver and require that the phone be activated in order to turn this Bluetooth receiver on. For phones like this, SAFR SCAN will not automatically detect the reader and transmit its credentials until turned on. While the user does not need to unlock the phone, they need to wake the phone in the manufacturer’s specific method such as pressing power button or tapping the screen.
3 Configuration
3.1 Configure SAFR Cloud Connect
See above for how to enable SAFR Cloud Connect
3.2 For Bulk Email, Enable SMTP Email Sending
Configure SAFR so that it can use an email server to send email messages.
- Get an SMTP Server account you can use to send emails.
-
Go to the Web Console's System Configuration page using one of following methods:
- Open http://localhost:8090/status
- SAFR Desktop > Tools menu > System Configuration
-
In theNotification Services Configurationsection
-
Click onSet up SMTP Email Service. You'll be presented with the following dialog.
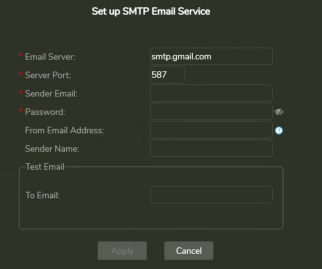
- Email Server: The address of the SMTP email server.
- Server Port: The email server port. The default port for SMTP is 587.
-
Sender Email: The email username of the SMTP account. (e.g.Susan.Johnson@gmail.com)
- Note: If you use 2-Step-verification with a gmail account, you need to create and use an App Password on your Google Account. For more information, seehttps://support.google.com/mail/answer/185833?hl=en.
- Password: The password for the SMTP account.
- From Email Address: The email address that will appear on the "From" line. This feature isn't supported by all email servers; if this field isn't used then theSender Emailvalue is used for the "From" line.
- Sender Name: The display name on the "From" line. (e.g.Susan Johnson)
-
Test Email: Configure the test email that will be sent after you finish setting up the SMTP email service.
- To Email: The email address to which the test email will be sent.
- Subject: The test email's subject.
- Body: The test email's body.
- ClickApply.
- Verify that the specified email address received a test email.
3.3 Configure SAFR SCAN
-
Set Access Mode to one of the Mobile Credential options

-
Enable SAFR Mobile Credentials in System > Mobile Credentials
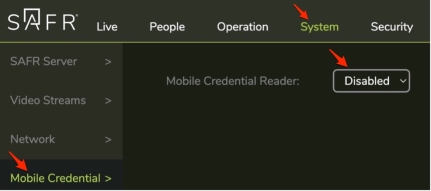
-
Set to Enabled and set following dialog
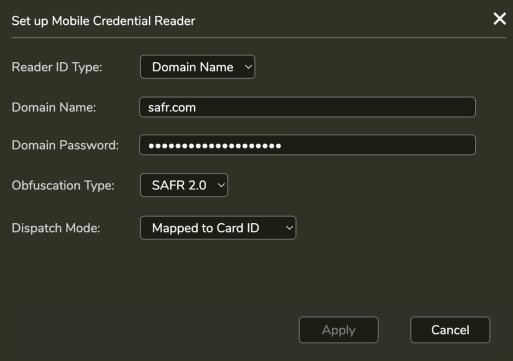
- Reader ID Type: Set to “Domain Name”
- Domain Name: Set to a unique string in the form of a domain name (letters, numbers or “.” only, no spaces).
-
Domain Password: This must be 20 characters and include at least one letter, one number and a special character.
- ⚠️ This password is used to encrypt SAFR Mobile Credentials so it should be kept secure.
- ⚠️ Once set, there is no way to view the password entered. Mobile Credentials are encrypted with this password and the same password must be used on the SAFR SCAN readers that accept this Mobile Credential. Losing the password would result in inability to create new Mobile Credentials that work with readers set to the valid password or adding new readers compatible with existing Mobile Credentials created with this password.
- Obfuscation Type: Set to “SAFR 2.0” which is compatible with latest SAFR firmware and supports the new embedded factors (adding card and face to the credential). Description of other Obfuscation Types is provided below.
- Dispatch Mode: Set to “Mapped to Card ID”. Dispatch mode defines the manner in which credential information dispatched to the control panel. Setting this to Mapped to Card ID (default) sends the access facility id and access card id to the panel as normal. This uses the Mobile Credential only for matching to person record and the transmits the access card credentials over Wiegand or OSDP.
4 Operation
4.1 Send Invite
-
Open Person Record and click “Invite to register” link above the Mobile Credential ID field.

-
This opens the a dialog.

-
Creating credential with Distributed Factors (no embedded factors)
- Reader ID: Select a ID (domain name) from the list. One will exist for domain name you have assigned to one or more readers configured for Mobile Credentials. See Configuring SAFR SCAN above for more information.
- Embedded add-on factors: Leave set to None. If selected other settings appear in this dialog as explained below.
- Send invitation to email: Email address of the user to be issued the credential.
- Make invitation valid for: Limits the during the credential can be redeemed. If the user does not generate the credential within this time the invitation must be re-issued.
-
Creating credential with Embedded Factors

-
Embedded add-on factors: Set this to either To include embedded factors. This encrypts PII information into the Mobile Credential when it is created on the user’s mobile device. This information is then decrypted at the reader and used to authenticate the bearer. Possible choices are:
- None – Do not embed any factors into the mobile credential
- Card – Embed the facility id and card id into the credential. The information is first
- Card and Face
- Revocation check: Set this if you want the credentials to expire and need to be renewed at the specified interval.
-
Embedded add-on factors: Set this to either To include embedded factors. This encrypts PII information into the Mobile Credential when it is created on the user’s mobile device. This information is then decrypted at the reader and used to authenticate the bearer. Possible choices are:
-
Click OK and SAFR will launch your email client with pre-populated messages as follows:

4.2 Cancelling an Invite
You can cancel an invite by returning to the person record and clicking Cancel invitation as shown below.
4.3 Accepting an Invite
-
Open email on Android or iOS device
- If SAFR Key App is not yet installed, user will be prompted to do so and should they accept will be taken to the appropriate page on the App/Play store.
-
During this process the user will be prompted to allow following permissions

-
The device will then prompt the user to grant these permissions thru a sequence of prompts. These permissions are required for SAFR Key to operate correctly.
⚠️ Location permission must be set to “Allow all the time” in order to allow granting access w/o requiring user to open the application (i.e. keep the phone in their pocket or bag). This setting is located under “Permissions > Location” in Android Settings. Options may vary, below is example:
* Enabling “Use precise location” is also advisable to allow
distance from device to be known more precisely. - After installing, go back to email and click invitation link again.
- Invitation link will launch the SAFR Key App and prompt user to create mobile credential.
-
User will be prompted to accept the credential as follows:

4.3.1 Taking Photo
If Face or Face and Access Card is to be embedded into the credential, user will be prompted to take a photo as described below.
|
Snap Photo |
Review Photo |
Invite Accepted |
|
|
|
|
SAFR Key reviews the photo for any flaws upon review. If any flaws are found, they are reported to the user and user is requested to retake the photo. Following are some common flaws that may be reported.
|
Center Pose |
Occlusion |
Lighting (Contrast) |
|
|
|
|
4.4 Gaining Access
Users are granted access when both factors (Face + Mobile Credential) are presented. By default, SAFR Mobile Credential is set to auto-send the credential to an authorized reader within BLE range of the phone. Below is an example of a SAFR Mobile Credential loaded in the SAFR Key app for Android.

As indicated in the screenshot, the credential was automatically sent to the SAFR SCAN reader. The reader is then awaiting the corresponding face in order to grant access.
While not advised, one can set the credential to manual send mode. Manual mode may be useful for testing in order to control when and if the credential is sent. By default, credential is sent every 60 seconds.
To set manual mode, click on the credential to view credential details.
|
Credential in Auto-send mode |
Credential in manual send mode. |
|
|
|
When in manual send mode, the “Send” button in details view can be clicked. You can also swipe to the right to manually send the credential (see screenshot below).

See section 2 above for how credentials are handled between the mobile device and the reader.
The reader will cache the credential for 60 seconds. Once the deice is out of range for longer than 60 seconds, the credential is discarded.
5 Special Topics
5.1 Using Mobile Credentials on Standalone Reader
SAFR Mobile Credentials can be used on a reader that is powered via 9-30 VDC and does not have ethernet connection. No data need be loaded on the reader at all. The reader need only be configured for mobile credentials on the desired domain and invitations sent to credential holders to create their mobile credentials on their phones. Reader configuration can be done over Bluetooth or the reader can be configured at installation time via a one time connection to ethernet. This section describes how to use SAFR SCAN in a fully standalone manor. It builds upon instructions provided above.
5.1.1 Enable Configuration over Bluetooth
-
Ensure SCAN Bluetooth connections are allowed.
- If SAFR SCAN is not connected to a server, Bluetooth are enabled by default. If needed you can change this in Security > Login over Bluetooth"
-
If SAFR SCAN is connected to SAFR Server, then Bluetooth connections are disabled by default. If needed you can change this in "Processor System Settings" for the SCAN device available through the Video Feeds window.

5.1.2 Connect and Configure SAFR SCAN for Mobile Credentials via BLE
- Open SAFR Mobile App for Android.
-
Click ☰ menu and in upper left and select "SCAN Devices Nearby". You will see a list of devices like the following:

- Select the SCAN device you wish to configure.
- Sign in using same credentials as created for browser login.
- Go to the Mobile Credentials configuration page.
- See above to configure the reader for mobile creds. Record the password and domain for below use.
5.1.3 Sent Mobile Credential Invites
A mobile credential invite must be sent from a SAFR On-Premises Server or SAFR Cloud account. Work with your SAFR Account Manager to obtain an account. Refer to instructions above for how to send out mobile credential invites. You must select option to embed Face or Face and Card to work with a standalone reader. Ensure you enter same password and domain as set on the reader.